Azure MFA for Enrollment in Intune and Azure AD Device registration explained
I have been working with setup of MFA required for enrollment in Intune a bit lately and have discovered a couple of things that is not really explained well in the Intune console/documentation.
Enrollment of devices in Intune will in most cases also trigger a device registration in Azure AD. This registration in Azure AD can easily be connected to a MFA requirement by just configuring your Azure AD to require MFA for device registration. But this does not apply to all scenarios, so in this blog post I am going to go into each platform and explain what happens during enrollment and how the MFA is triggered. I will also cover different options for enrollment of Windows 10 Mobile.
SETUP AZURE MFA FOR DEVICE REGISTRATION AND AAD JOIN
First thing you need to do is to enable MFA either in Azure MFA or on your ADFS. In this scenario I will only use Azure MFA and the setup described here will also work if you are using ADFS federation but still want to use Azure MFA.
The scenario described here is based on you having a EMS license and therefore also Azure AD Premium for your users.
The first thing we do is to add an MFA Provider in Azure AD. You go into you Azure AD console and go to Multi-Factor Authentication Providers and click on Create a new MFA Provider.
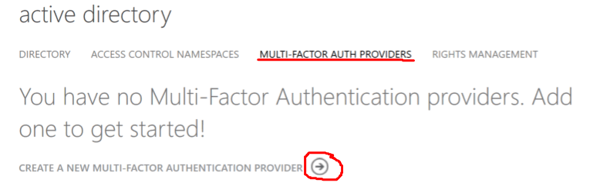
Then, you will go to the QuickCreate part and you will name your MFA Provider and choose your Usage Model and link to your directory. I have EMS for all my users and choose Per Enabled User.
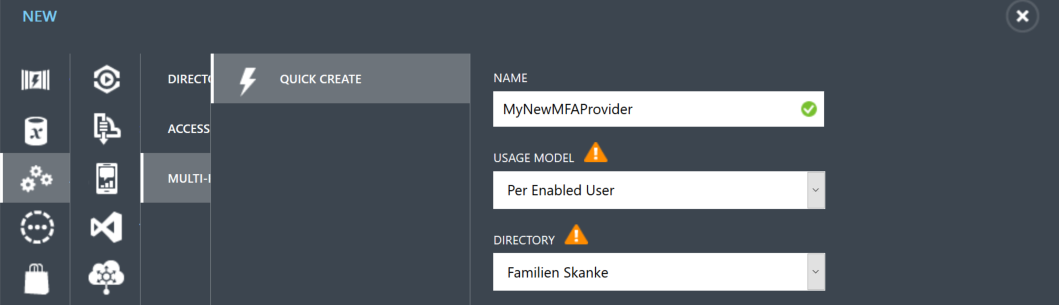
Now on the bottom of your page you can click on Manage to change settings for your MFA Provider. There is no need to actually change anything here for MFA to work. But this is the place to see usage and status.
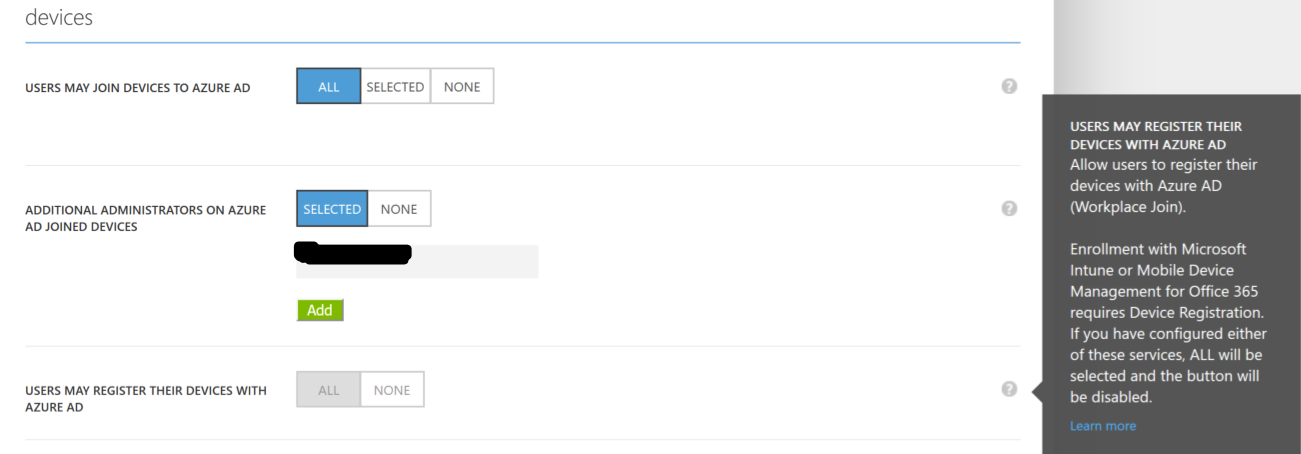
The next thing we need to do to require MFA for device enrollment is to go into the configuration of your Azure AD and locate the Devices section. I presume that you have already enabled Intune in your tenant and that the option “Users may register their devices with Azure AD is already set to All and locked. I have also setup that users may use Azure AD Domain join in my tenant.
No to the important setting that you need to apply. Require MFA to join devices.
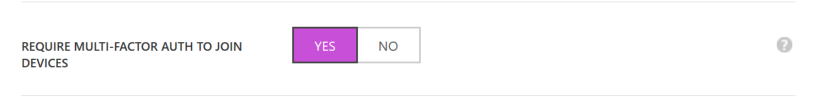
Now you are setup for require MFA for both Device Registration via Intune and also for Azure AD Domain join. There is no need for enabling MFA for specific users and you really should not enable it for specific users in this scenario if you don't want users to be required MFA for all access to Azure AD resources (Office365 and so on)
Regarding Windows 10 Mobile you should read on. There is some important steps you need to consider when it comes to that platform specifically.
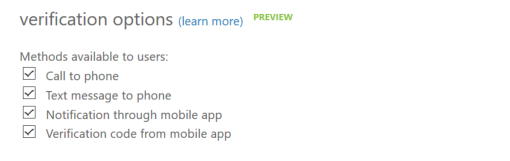
Today, as far as I know, there is no way to provision the authentication details setup for your users from AAD Connect sync, or to set this up in the cloud for synchronized users. You can as administrator manually set this details in Azure AD for cloud users. So, normally the users will on first attempt be required to setup that kind of information. You can also decide on verification options by clicking on the “Manage Service Setting” under Multi-Factor Authentication in Azure AD Configuration.
ENROLLING IOS OR ANDROID DEVICE WITH MFA
When you enroll a iOS (iPhone/iPad) or Android device in Intune it will also in the back end register the device in Azure AD. This all happens when you log into the company portal app and choose to register your device. It is important to understand that it actually is this back end registration in Azure AD that triggers the MFA challenge when enrolling the device. Intune itself doesn't really have MFA as part of it setup for other platforms than Windows Phone 8x/Windows 10 Mobile.
The device registration in Azure AD is a required steps for these platforms so the user will not be able to enroll into Intune without actually be MFA challenged. The only time this might clinch is if a user un-enrolls a device and then enrolls it again while the device still is registered in Azure AD. I have seen this a few times, but I think this is a testing scenario and that users really don't un-enroll and enroll that quick in real time scenarios.
ENROLLING WINDOWS 10 MOBILE DEVICES WITH MFA
To enable Windows 10 Mobile enrollment by adding a work account you also need to enable AUTO registration with Intune in Azure AD.
Go into your Azure AD and choose Applications and then choose Microsoft Intune
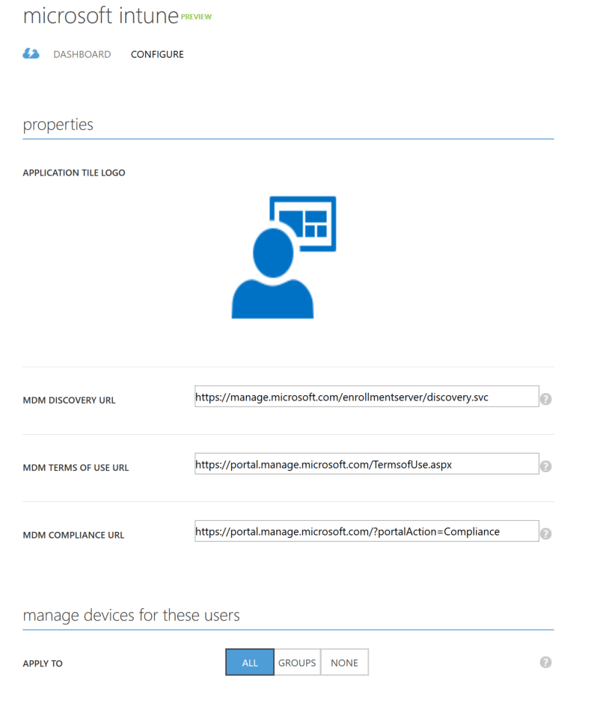
The configuration should be like this to enable this scenario for all users, but you can also just choose a group of users to enable this for.
Option 1 Enroll into Intune by adding a Work Account on your phone:
1. Go into Settings – Accounts – Work Access on your phone.
2. You will see “Sign in to Azure AD” – Add or remove a work or school account
3. On the bottom of this next page you will see Add a work or school account
4. Now you log in with your account and the MFA Challenge kicks in.
5. Depending on your setup you might me asked to provide a Work-pin. This is only if you have Passport for Work enabled in your Intune tenant.
6. Registration is complete.
By having this setup what you actually do is that you do a Workplace join of your phone to Azure AD, this triggers the MFA. This setup of Microsoft Intune application in Azure AD triggers a policy to the device forcing it to enroll the device in Intune as well. All good so far.
But. There is another option on Windows 10 Mobile as well. And if you don't to additional steps in your Intune Tenant this will not trigger MFA for the enrollment.
Option 2 Enroll into Intune by the Enroll into device management option:
1. Go into Settings – Accounts – Work Access on your phone.
2. Go to the bottom of the page and you will see Enroll into device management.
3. Now provide your email address (or UPN) and click on Connect
4. Next page you provide your password and sign in.
5. Now you actually are enrolling into Intune, but you will notice that there was no MFA challenge and you don't have the Work Account on your device either.
So why is it like this? And what to we do?
In Windows 10 the experience of adding a work account is not only accessible through Settings but also happens automatically as part of setting up an application for work for the first time like if you setup your email account in outlook with your work email. That means that if you setup work email or connect to Onedrive for business you will be able to force the device into management by having the setup of the Auto-MDM enrollment setup.
If you use option 2, you will only enroll in Intune. There is no Azure AD device registration involved like it is on the other platform. That is why Azure AD isn’t able to challenge the user with MFA. But there is a solution to this as well.
Log in to your Intune tenant and go to Admin – Mobile Device Management and Multi-Factor Authentication and click on Configure Multi-Factor Authentication:
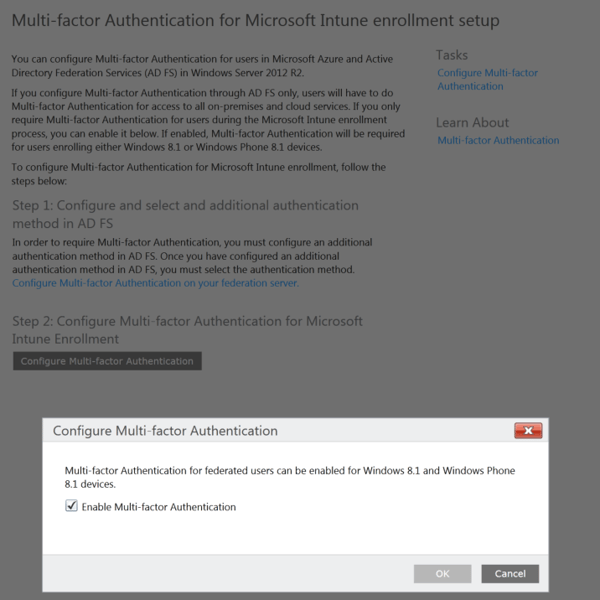
As you can see now, there is a lot of text on this page talking about step 1 with ADFS setup and so on, but that is really not important in this scenario when we are using Azure MFA in the cloud. Configuring MFA requirement for enrollment in Intune, just tells AAD that MFA is needed to complete the authentication request. Azure AD handles this in different ways:
1. For cloud or managed domain user, if Azure MFA is configured AAD will do MFA (no ADFS involved). If Azure MFA is not configured, the registration will fail.
2. For a federated user (ADFS), if ‘supportsMFA’ is turned OFF for the federated domain setting, AAD will redirect the user to the IDP (say ADFS). On the response, if the user is configured for Azure MFA, Azure MFA will then do the 2nd factor authentication. If Azure MFA is not configured it will fail.
3. For a federated user, if ‘supportsMFA’ is turned on in the federated domain settings, AAD will then redirect the user to the IDP and in the request ask it to do MFA. ADFS will then proceed to do MFA (fail with error if there is failure) and then send a token to AAD with an MFA claim. AAD examines this claim and then makes the decision to allow the enrollment request to flow through or error.
Now finally you have MFA for all your available Intune Enrollment and also Azure AD Domain Joins set up and required.
Senior Consultant
Senior Consultant at Innofactor (formerly Lumagate). He specializes within Enterprise Mobility Management, Windows Client, Security and Cloud Identity. Delivering both technical workshops and advisory to customers is something he loves to do. He also has long experience as speaker at technical events locally in Norway.


