Configure integration between Apple DEP and Microsoft Intune
For a while now, Microsoft Intune has supported Apple Device Enrollment Program (Apple DEP), which is a part of the Apple Deployment Programs together with Apple Volume Purchase Program (Apple VPP). With Apple DEP, businesses and educational institutions can easily streamline deployment and configuration of iOS and OS X devices purchased either directly from Apple, or through any authorized resellers. By automating the initial setup with Mobile Device Management enrollment, Apple DEP simplifies the whole process and even allows you to skip certain Setup Assistant screens. For certain businesses and especially educational institutions, with Apple DEP you have the option to wirelessly enable something called Supervised mode, giving you the possibility to provide a higher level of device management in terms of additional restrictions like turning off iMessage, Game Center or AirDrop. Further it also gives you the option to enable what’s called Single App Mode, restricting the device to only allow for instance Safari to be launched. With Apple DEP, you can perform large-scale deployments of iPads and iPhones in your organization seamlessly with zero involvement from the IT department.
Now that all sounds really great, so how can we leverage all this with Microsoft Intune? That’s exactly what I’m gonna cover in this blog post.
NOTE! In this post, some screenshots have been altered to conceal certain information since they originate from a customer production environment. I would like to give a big thank you for letting me use your environment enabling me to write this post. You guys know who you are!
Overview
Before we get started, I just want to talk about what we’re gonna cover in this post. Since there’s to many different scenarios to dive into, I’ve chosen to outline the required setup and configuration to get going with Apple DEP and Microsoft Intune, from a corporate-owned device scenario. Below is the high-level process that I will cover:
- Sign up for Apple Deployment Programs
- Configure integration between Apple DEP and Microsoft Intune
- Create Corporate Device Enrollment profile
- Manage purchased devices in Apple DEP
SIGN UP FOR APPLE DEPLOYMENT PROGRAMS
If you’ve ready my blog in the recent weeks, you may have come across my posts about Apple VPP. In one of those posts, I talk about signing up and creating a new Apple ID for the Apple Deployment Programs. If your business or organization already have such an Apple ID tied to the Apple Deployment Programs, I suggest that you use that when configuration integration between Apple and Microsoft Intune, or at least designate desired administrators to sign up for an Apple ID that will become an Admin in the Apple Deployment Programs. If you do not have any Apple ID as of yet, follow the sign up (or enroll like it says on the website) process by going to the following website from Apple:
With that covered, let’s have a look at how we can configure the integration between Apple DEP and Microsoft Intune.

CONFIGURE INTEGRATION BETWEEN APPLE DEP AND MICROSOFT INTUNE
To configure the integration between Apple DEP and Microsoft Intune, you’d need access to the Apple Deployment Programs portal, specifically the Apple DEP part of it which requires an enrolled Apple ID. I can’t stretch this enough, since it can sometimes be confusing with all those Apple ID’s back and forth. In the Apple Deployment Programs portal, we first need to add a MDM server, which will be our Microsoft Intune tenant in this scenario. This requires us to download a specific encryption key from Microsoft Intune, specify it when adding the MDM server and finally upload a DEP token back into our Microsoft Intune tenant. Let’s take a look at how all of this can be accomplished:
1. Login to manage.microsoft.com with your tenant administrator account (normally your Global Administrator account)
2. Go to Admin workspace, expand iOS and Mac OS X and select Device Enrollment Program.
3. Click on Download Encryption Key and save the file as e.g. AppleDEP.pem in any location.
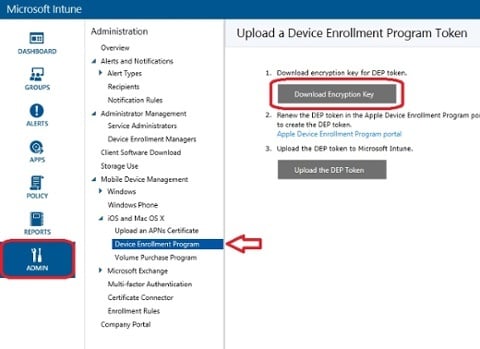 4. Login to deploy.apple.com with your enrolled Apple ID.
4. Login to deploy.apple.com with your enrolled Apple ID.
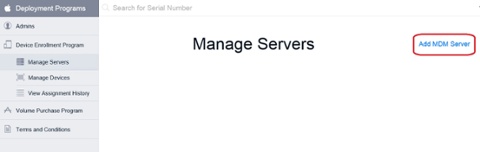
5. In the menu to your left, click on Device Enrollment Program and then Manage Servers.
6. Click on the Add MDM Server link on your right.
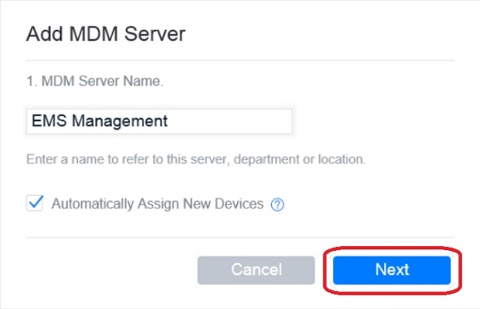
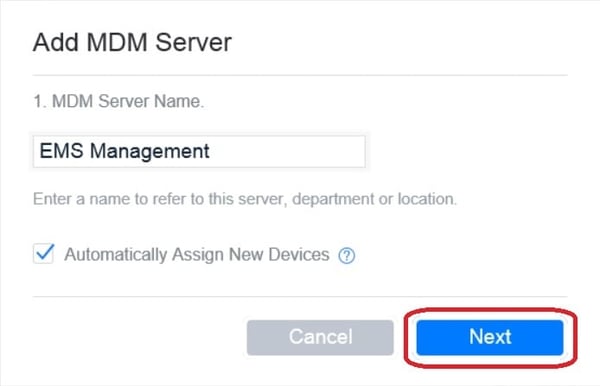
7. Give your MDM server a name, it doesn’t matter really what you go with. At this point, you also have the option to select whether devices bought through Apple directly or authorized resellers that have been tagged for Apple DEP should be assigned directly to this MDM server. If you do not select this, you’ll have to manually assign purchased devices, either by specifying their serial number, locating an order number or by uploading a CSV file. I’d highly recommend that you automatically assign your devices, since it will stream line the overall process even further. Click Next.
8. Click on Choose File and select the downloaded encryption key file called AppleDEP.pem and click Next.
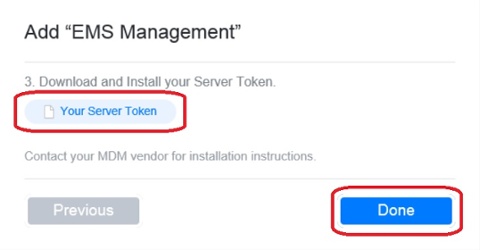
9. Click on Your Server Token to download to any location. When you’ve successfully downloaded your server token, click Done.
10. Back in the Intune Admin portal, click on Upload the DEP token.
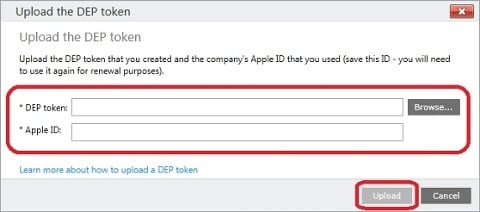
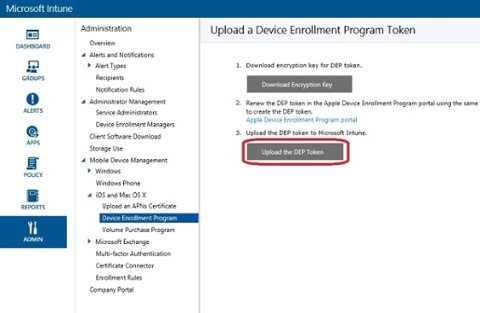 11. Browse for the p7m file downloaded from the Apple DEP portal and enter the Apple ID used to add the MDM server. Since I’ve taken the screenshots from a production environment of one of my customers, I cannot show you how it looks from here on when you click on the Upload button, but I’m quite sure that you’ll understand what’s gonna happen. Click Upload and in the event you’re prompted, simply confirm the action.
11. Browse for the p7m file downloaded from the Apple DEP portal and enter the Apple ID used to add the MDM server. Since I’ve taken the screenshots from a production environment of one of my customers, I cannot show you how it looks from here on when you click on the Upload button, but I’m quite sure that you’ll understand what’s gonna happen. Click Upload and in the event you’re prompted, simply confirm the action.
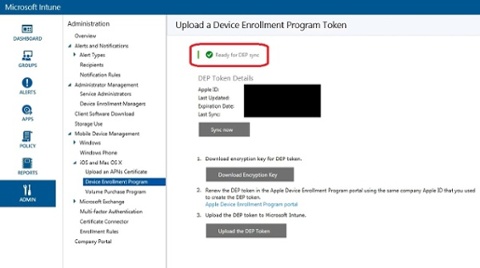
12. Once you’ve uploaded the DEP token, you should see a green check mark telling you that Microsoft Intune is ready for DEP sync.
The integration between Apple DEP and your Microsoft Intune tenant has now successfully been configured. Next up we’ll create a Corporate Device Enrollment profile and make it the default one for devices synced from Apple DEP to Microsoft Intune.
CREATE A CORPORATE DEVICE ENROLLMENT PROFILE
In order to enroll corporate-owned devices tagged for Apple DEP, you need to create a Corporate Device Enrollment profile, that will be used by the Setup Assistant (out-of-box experience on iOS devices). This profile can be used to define certain use case scenarios for how the iOS devices are going to be used in your organization. For instance, let’s say that you have two scenarios:
- Corporate-owned devices that are unsupervised daily usage by end-user.
- Kiosk devices that may run in the Single App Mode, only used for specific tasks like accessing a web application
To support both of these scenarios, you’ll need to create different Corporate Device Enrollment profiles. If you only have a single scenario for how your Apple DEP tagged devices are going to be assigned in your organization, a single profile should suffice. One thing to be aware of though, is that you can only have one of your Corporate Device Enrollment profiles as your default. So to support both of the mentioned scenarios above, it’d be recommended to set the Corporate-owned profile as the default, and manually assign devices targeted for the other scenario with that particular profile.
1. In the Intune Admin portal, go to the Policy workspace, click on Corporate Device Enrollment and click Add.
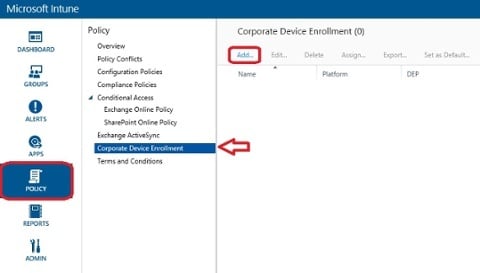
2. Name your profile something that suits the desired scenario, like Corporate-owned Devices. Select a Device group (I’ve already created a group, and will not cover that part in this post). One thing to be aware of here, if you choose No user affinity, you could get into trouble. Only select that in scenarios for e.g. kiosk devices where there’s no need for user affinity. Click the slider for Device Enrollment Program settings.
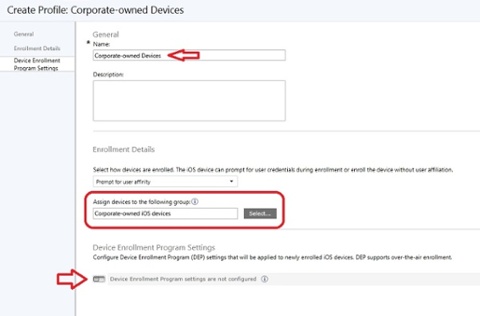
3. Enter your IT/Helpdesk department name and support number. Select whether to put the devices in Supervised or Unsupervised mode. If configured for Supervised mode, you have an additional option to select to lock the enrollment profile to the device, meaning that the end user cannot un-enroll the device (which would be suitable since it’s a corporate-owned device). Make the suitable selection for the Setup assistant panes that will be showed during the out-of-box experience. When ready, click Save Profile.
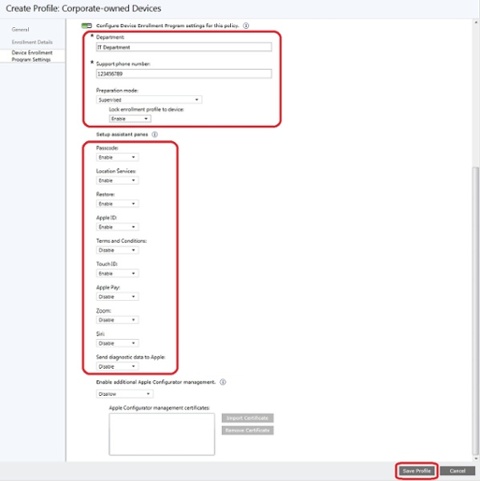
You’ve now created your first (and default) Corporate Device Enrollment profile.
Next up I’ll cover some basics on managing purchased devices in Apple DEP.
MANAGE PURCHASED DEVICES IN APPLE DEP
As I’ve previously touched slightly in this post, you have 3 methods of assigning devices tagged for Apple DEP with your DEP Customer ID to your MDM server (your Microsoft Intune tenant). I’m not gonna cover them all, since they’re pretty straight forward, and if you’ve configured your MDM server for automatic assignment, this step is not required. However, in the event that you’ve bought a number of lets say iPhones, and you’ve been given an order number (or even if you’ve lost that order number), we can in the Apple DEP portal search for these devices and assign them to a MDM server. By assigning devices like this, Microsoft Intune will be able to sync the device information and later on apply a Corporate Device Enrollment profile to those devices.
1. In the Apple DEP portal, select Manage Devices and for demonstration purposes, my customer had just recently purchased an order of 97 iPhones, where 96 of them where unassigned. So to assign these to a MDM server, choose by Order Number and write All available in the text field. Choose your MDM server and click OK.
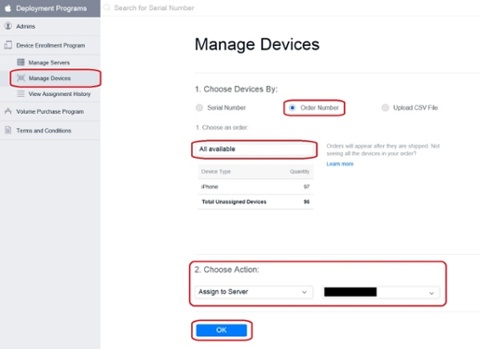
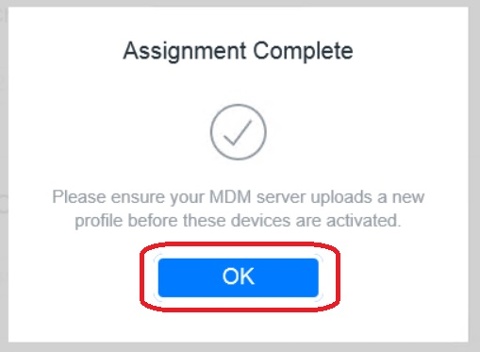
2. In the prompt that appears, click OK. Your assignment has now been completed.
3. If you go to the Intune Admin portal again, in the Admin workspace under iOS and Mac OS X, select Device Enrollment Program and click Sync now.
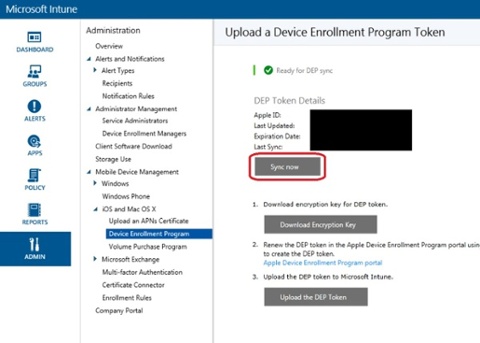
4. A synchronization request has now been sent to Apple. This step is not a requirement, but it will speed up the process for this demonstration.
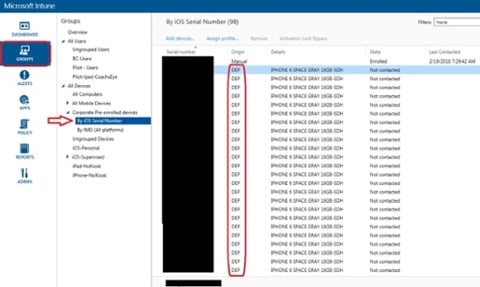
5. Go to the Groups workspace, expand Corporate Pre-enrolled devices and select By iOS Serial Number. Once Microsoft Intune has synced with Apple DEP, your devices will appear like shown in the picture below.
SUMMARY
Like I’ve shown you now in this post, Apple DEP can really streamline the process of how you manage corporate-owned devices. I suggest that you make a decision for your organization on how to handle such devices, and if Apple DEP is the right choice for you.
Principal Consultant and Enterprise Mobility MVP
Principal Consultant and Enterprise Mobility MVP. Nickolaj specializes in Enterprise Mobility and Security, Windows deployments and Automation. Additionally, he has extensive experience with planning, implementing and migrating System Center Configuration Manager environments on a global scale. Nickolaj has also been awarded as PowerShell Hero 2015 by the community, is the author of ConfigMgr Prerequisites Tool and a frequent speaker at user groups.


