Massive ransomware campaign hits victims in at least 100 countries. What is it, and what do you do?
Today, many of our customers and the critical systems they depend on were victims of malicious “WannaCrypt” software. Microsoft worked throughout the day to ensure we understood the attack and were taking all possible actions to protect our customers. Lumagate has helped customers during this horrible attack and we are doing our best to clean up and update systems.
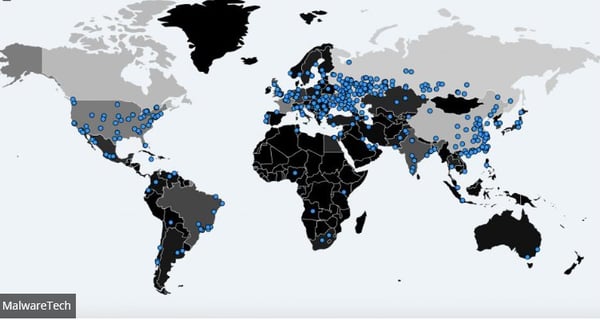 WannaCry infections (Picture from MalwareTech)
WannaCry infections (Picture from MalwareTech)
What is it?
The attack seems to be using the NSA exploit leaked by Shadow Brokers (EternalBlue which uses a vulnerability in the SMB Protocol to spread).
This means that unpatched systems are spreading this ransomware internally on the network.
Some of the observed attacks use common phishing tactics including malicious attachments. So, all your users should use vigilance when opening documents from untrusted or unknown sources.
What can I do to prevent it?
1. Patch all your systems
To get the latest protection from Microsoft, upgrade to Windows 10. Keeping your computers up-to-date gives you the benefits of the latest features and proactive mitigations built into the latest versions of Windows.
You need to have a good patching process to patch your systems this would most likely stop the spread of this malicious code.
Here is the patch: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Microsoft has also released security patch for non-supported platforms like Windows XP, Windows 8 and Windows Server 2003. (Customers running Windows 10 were not targeted by the attack today.) Download the update here: http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
2. Enable Office 365 ATP (Advanced Threat Protection)
Protecting against unsafe attachments. All suspicious content goes through a real-time behavioural malware analysis that uses machine learning to evaluate the content for suspicious activities.
Unsafe attachments are sandboxed in a detonation chamber before being sent to recipients
Protect your environment when users click malicious links. The URL s are examined in real time when a user clicks them.
Read more here: https://products.office.com/en/exchange/online-email-threat-protection
3. Security Awareness
Most likely this attack started by an email (well multiple emails) but assume someone clicked on a link named invoice or something else “interesting”. Security awareness is still very common to be overseen by security teams and IT departments in general
We can’t simple protect against every bad thing by technical means and we need to raise the awareness for the end users.
Make sure to kick off a Security awareness program, this could be seminars, intranet information.
Right now; Send out an email to your organization and tell them to be _very_ caution about suspicious emails and attachments.
4. Segmentation
Make sure you have network segmentation to avoid spreading.
Use a Local Firewall to block traffic, usually there is no need to have SMB open against clients.
5. Privileged Access
Separation of duties
Privileged Access Management (PAM - https://docs.microsoft.com/en-us/microsoft-identity-manager/pam/privileged-identity-management-for-active-directory-domain-services )
Users should only have access to what they need.
Don’t set up a share where all users can read and write files from all departments.
6. Windows 10 Device guard
Blocking untrusted code from execution. For enterprises, use Device Guard to lock down devices and provide kernel-level virtualization-based security, allowing only trusted applications to run, effectively preventing malware from running.
7. Read information
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks
General information on ransomware: https://www.microsoft.com/en-us/security/portal/mmpc/shared/ransomware.aspx
MS17-010 Security Update: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
What if we are already attacked?
1. Disable SMBv1
Disable SMBv1 with the steps documented at Microsoft Knowledge Base Article 2696547. https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
2. Add firewall rule
Consider adding a rule on your router or firewall to block incoming SMB traffic on port 445.
3. Install the MS17-010 immediately on all systems
Windows 10 and 2016: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Windows XP, Windows 8 and Windows Server 2003: Http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
4. Contact us for help
Lumagate has extensive experience in helping customers that are attacked and of course how to prevent it. Let us know if you need help, we are standing by.


