The future of sync from your on-premise to Azure AD
The synchronization engine used to synchronize your on-premise Active Directory to Azure AD has changed quite a bit the last years. First out was “Dirsync”, followed by “AADSync” and now “Azure AD Connect” – all of which have added features such as synchronizing from multiple AD forests and automatically setting up federation. Dirsync and AADSync are soon to be deprecated. Here are some of my thoughts on what the future might bring when it comes to sync.
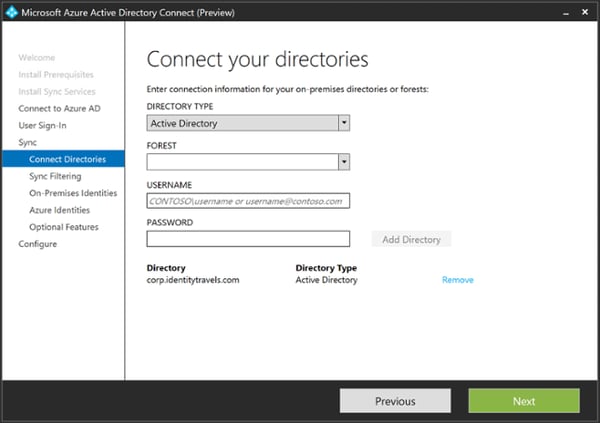
The first interesting thing we find when installing Azure AD Connect Preview 2, is that “Directory type” is a drop down menu, currently with “Active Directory” as the only option. It has already been stated on the AD Team blog that LDAPv3 directories will be added as a supported source, and since the synchronization engine in Azure AD Connect is based on Forefront Identity Manager, we might see other types of sources added here later as well such as SQL or SAP.
Why? Microsoft is planning for the cloud only enterprise, and with Azure AD Join in Windows 10, you can actually do quite a lot without actually having an Active Directory.
There are quite a few interesting features available now in this version, let us look at a few of them.
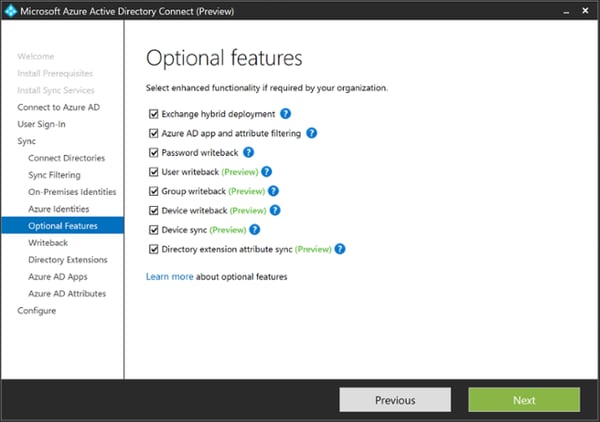
As you can see, it is all about writeback.
User writeback means that all users added to your Azure AD will be created in an OU in your on-premises Active Directory as well, and because of password writeback they will have the same password as in Azure AD as well.
What Microsoft is planning here is that Azure AD will become the hub of all your Identity and Access Management (IAM) tasks. There are already the example of the Workday HR System that has direct provisioning to Azure AD, meaning that if you combine this with user writeback, users from this HR system would actually also get an Active Directory account on-premise. My inner FIM consultant is a bit afraid of this feature.
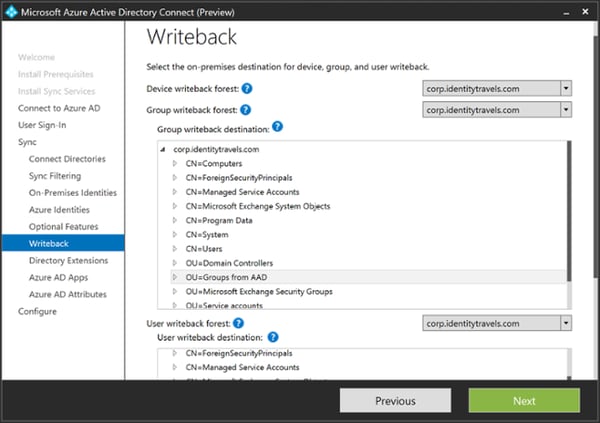
Group writeback is actually currently not what you would expect (at least not what I expect). It does not write back all groups from Azure AD to your on-premises Active Directory in the same way user writeback does for users, but it writes back “Office 365 Groups”, which is a special SharePoint + Email + Lync hybrid type of group used for collaboration.
I expect this group writeback feature to be expanded to include regular Azure AD security and distribution groups as well. This makes sence, as this is a killer feature when combined with Azure AD Premiums self service features for groups.
The last type of writeback is device writeback. This takes all of your InTune enrolled devices and writes them as a device in your on-premises Active Directory. The reason why you would want to do that is to combine this with the Web Application Proxy (WAP) of Active Directory Federation Services (ADFS). This way you can publish your on-premises web applications, such as SharePoint, and still being able to check for device compliance even though the device is enrolled into InTune. This can also be done using the Azure AD Application Proxy.
What I expect for device writeback in the future, is for Azure AD Joined Windows 10 devices to be automatically synced back to AD as well, and being able to use the same functionality.
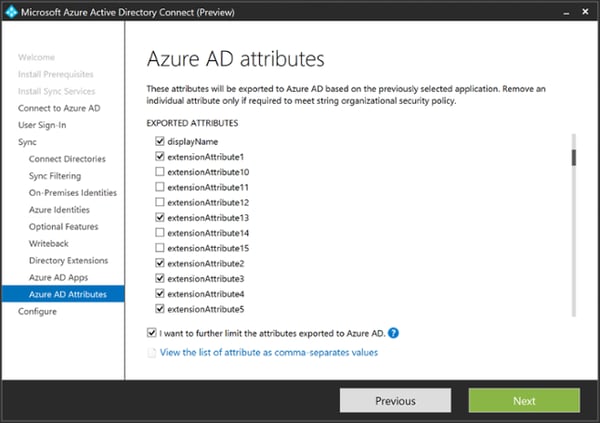
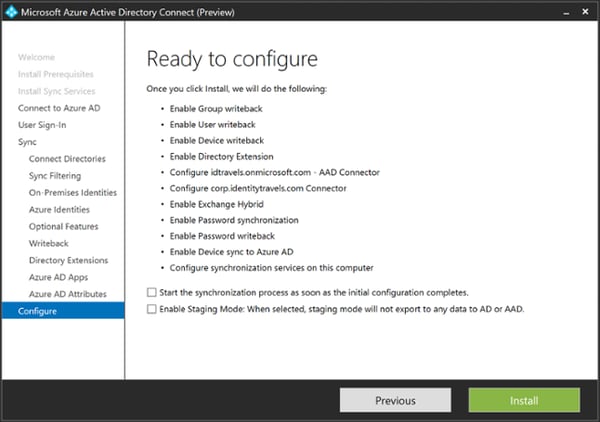
As you can see from many of these features, Microsoft is now enabling organizations to actually be cloud first, and have Azure AD as the source of identity, instead of using their on-premises AD as the source.
Just for afterthought - Imagine combining HR direct provisioning to Azure AD, with group self service and both user and group writeback to AD. What do you get?
Team Lead Identity Access and Security + Principal Solutions Architect
Marius is Team Lead Identity Access and Security + Principal Solutions Architect in Norway focusing on identity


