Who is trying to access your domain? And who succeeded!?
With more than a 44% raise in documented successful cyber-attacks in 2017*1 all companies should consider if they are next or already compromised.
Since most of the breaches are coming from hacking, almost 60%, companies should be watching for suspicious behavior or indicators about possibly reconnaissance or direct attacks. By using Event Viewer, firewall logs and other similar tools it is almost impossible to spot the few bad failed authentication attempts amongst all the good ones that are trying to exploit security flaws, trusting users on the internet or internet facing services that are exposing you AD directly or indirectly.
So how can we gain insights as to whether we are in the danger zone or all clear? Or even better how can we protect our business against these attacks?
There are a few rock-solid options that will keep all your data safe:
- Disconnect your business from the internet (Partial secure)
- Disconnect your servers from your users and the internet
Ok, these are not really options, so what can we actually do?
Well there are a few good options and one of them is start using Microsoft ATA or Azure ATP. These products are built specifically to spot attacks or reconnaissance attempts in an easy to use web managed portal.
Microsoft ATA is the on-prem version of Azure ATP. ATA only knows about local AD whereas ATP takes data from your Office 365, Exchange Online, Azure AD, AD and Windows 10 Clients with Defender ATP and more to come.
Microsoft ATA
Microsoft ATA is your never sleeping, always evolving and always alert security officer. It will integrate with your domain controller, existing SIEM and syslog serves and with behavioral analysis, deep package inspection and knowledge from several hundred billion authentications, emails and more than one billion devices every month*2 it can quickly spot if someone or some process is trying to penetrate your security measures.
Microsoft ATA will detect:
- Pass-the-Ticket (PtT)
- Pass-the-Hash (PtH)
- Overpass-the-Hash
- Forged PAC (MS14-068)
- Golden Ticket
- Malicious replications
- Reconnaissance
- Brute Force
- Remote execution
- … and more
New detections are added to the list as new techniques are discovered.
It will give you insights as to where its coming from and who is the victim with easy drill-down to see what was tried or what was compromised. Simply holding the mouse over fx the “6 resources” will show you what resources have been access in a small overlay
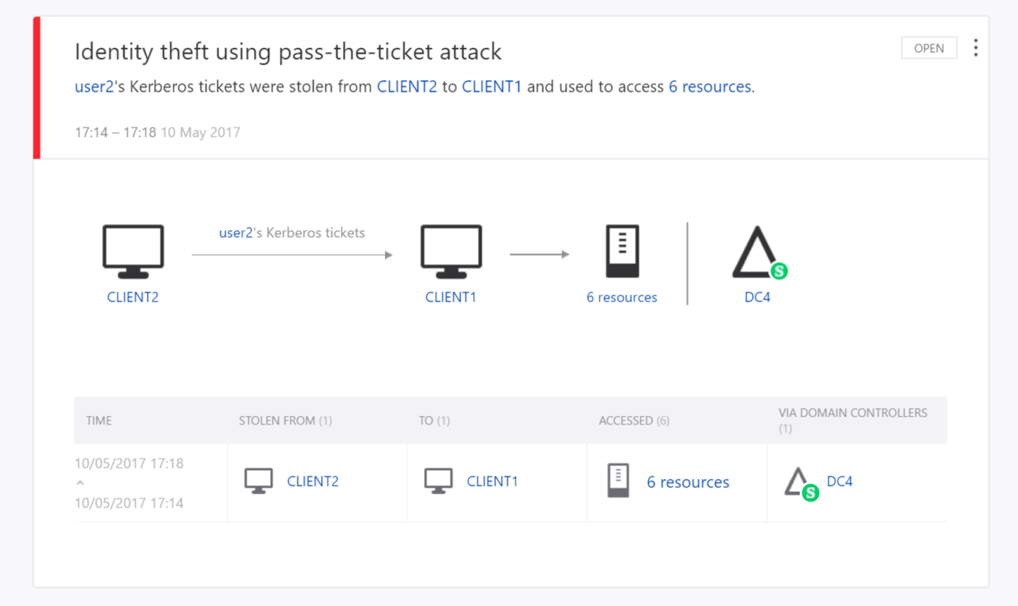
It will also warn about suspicious behavior that could indicate a hacker is mapping out your environment. Here is an example of a potential hacker trying to map internal resources with specialized DNS queries that would not normally occur in your environment.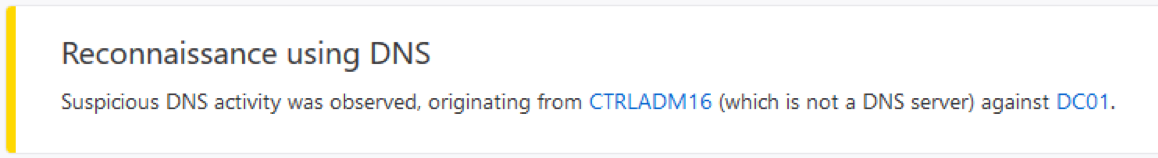
If you have an Enterprise Agreement with Microsoft then you probably already have the rights to use this product already.
Azure ATP

Microsoft ATA’s leaner, meaner and bigger brother that has your entire hybrid environment covered. It has the same features as ATA, many of Microsoft’s cloud offerings such as Azure AD, Exchange Online and Defender ATP date and with a lot more in the pipe.
Microsoft ATP will give you insights across your entire enterprise whether the source is clients inside your enterprise, mobile workers, remote offices, Online Outlook, Office 365 Online users or RADIUS account from VPN’s.
These are some examples of what it will detect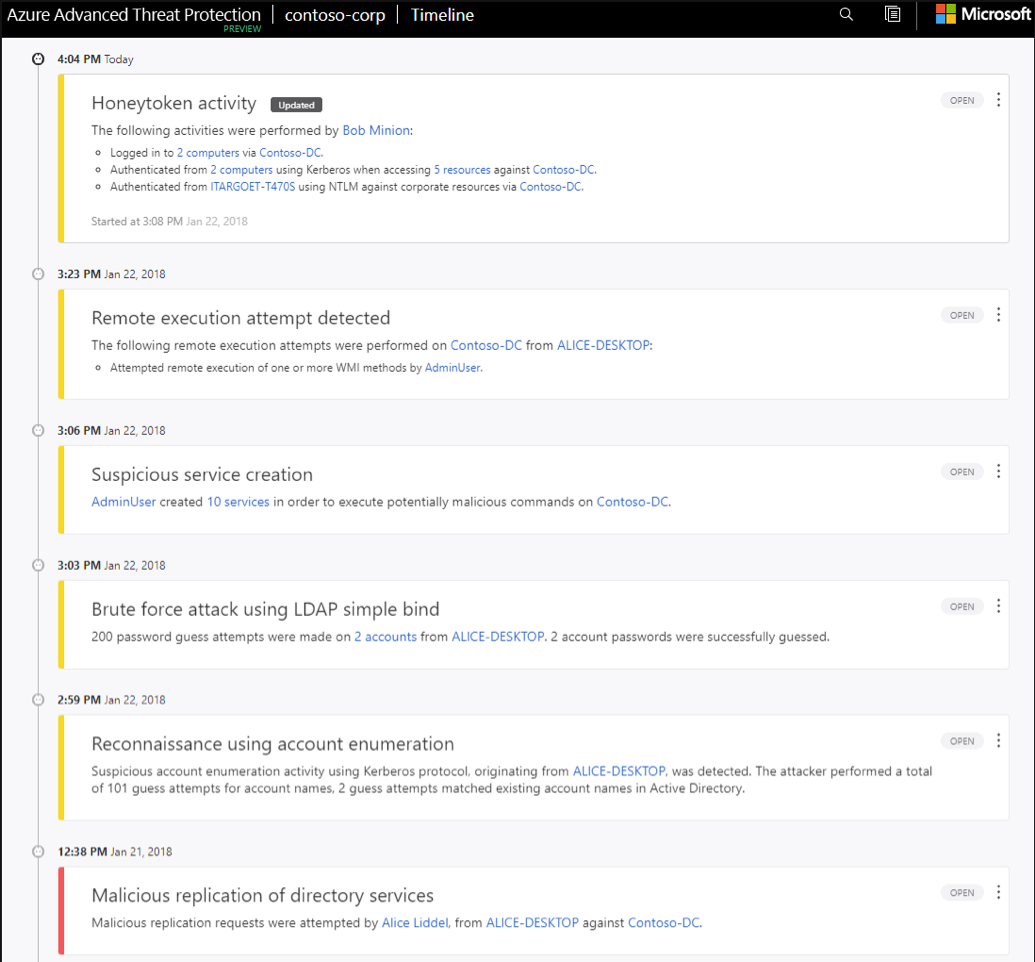
With this insight it is now possible for people that are not knee-deep in security forensics to identify and respond to threads coming from anywhere in your hybrid environment. With easy to use, noise filtered views of what’s going on across your entire workforce no matter where they are or how they connect to your business.
Licensing
You can purchase Advanced Threat Analytics (ATA) either standalone with a Client Management License (CML) available per user or per Operating System Environment (OSE) or through one of the following Microsoft license suites that provide multiple Microsoft products or cloud services at a significant discount over standalone license prices:
- Enterprise Client Access License (ECAL) Suite
- Enterprise Mobility Suite (EMS)
- Enterprise Cloud Suite (ECS)
Azure ATP is licensed through the EMS E5 or Microsoft 365 E5 licensing that can be purchased directly from the Office 365 portal or through you normal Enterprise channels.
If you find any of this information exciting, interesting or maybe even a bit frightening then feel free to contact us and we will help you with more information, get it up and running or just have a meeting with your options and further information.
Further Reading:
Microsoft ATA
https://www.microsoft.com/en-us/cloud-platform/advanced-threat-analytics
Azure ATP
https://azure.microsoft.com/en-us/features/azure-advanced-threat-protection/
Windows Defender ATP
https://www.microsoft.com/en-us/WindowsForBusiness/windows-atp
Office 365 / Exchange Online ATP
https://products.office.com/en/exchange/online-email-threat-protection
References:
*1 https://www.idtheftcenter.org/2017-data-breaches
*2 https://www.microsoft.com/itshowcase/Article/Content/934/Microsoft-uses-threat-intelligence-to-protect-detect-and-respond-to-threats
*3 https://docs.microsoft.com/en-us/advanced-threat-analytics/what-is-ata
Senior Consultant
Stefan is a Senior Consultant and Microsoft Professional who focuses on Security, Cloud and Infrastructure. He specializes in secure cloud solutions build around Azure’s SaaS, PaaS and IaaS framework with a focus on Infrastructure and usability. He has made solutions for governmental institutes, large companies and SMB with a focus on security, scalability and end-to-end optimization with a ability to think out of the box driven by innovation



